According to Verizon’s 2021 Data Breach Investigations Report (DBIR), over 80% of hacker attacks are due to either brute force cracking or the use of leaked credentials.
Source: https://www.verizon.com/business/resources/reports/dbir/
- Which is certainly due to the fact that Internet criminals can already acquire such data on relevant marketplaces for little money.
- and the fact that users are getting tired of passwords. On average, a normal Internet user now has 190 user accounts and certainly doesn’t think up a password that is also unique for every access.
This makes it all the more important that companies take measures to ensure that their systems are protected against unauthorized access in the best possible way. Particularly in times when home office work is the order of the day.
As professionally used issue and project management systems are often web applications that can be conveniently accessed via the Internet and are often only shielded from the outside world with the help of a password-protected user login. It can be assumed that here, too, the credo regarding password selection applies among a large proportion of employees: convenience takes precedence over (data) security.
Trust is good, control is more important
Controlling user accounts is important for companies because their economic existence may depend on it. Those who actively manage their user accounts have a chance of ensuring that inactive or forgotten user accounts do not mutate into a vulnerability.
Attacks on company-relevant, sensitive data are only possible because it has never been so easy to abuse forgotten accounts of former employees, customers or suppliers. This is because such attacks are usually difficult to detect.
Therefore, companies cannot avoid regularly reviewing and updating the internally implemented, necessary data protection rules for their employees.
Protect Redmine user accounts from abuse
For Redmine users we have a few tips and solutions to make this task easier. Some of them are already implemented in Redmine by default, others can be used by additional plugins.
Force password change
In the Redmine configuration it is possible to force a password change when authenticating by password. To do this, set the selection from locked to one of the available values between 7 and 365 days.Enable two-factor authentication (2FA).
For example, the german BSI recommends enabling two-factor authentication as an additional security measure as soon as it is possible. The current Redmine versions support 2FA for users as an authentication measure. In the Redmine configuration, you can choose between the options locked, optional, required here. At least for users with administrator rights it is recommended to enable the option required.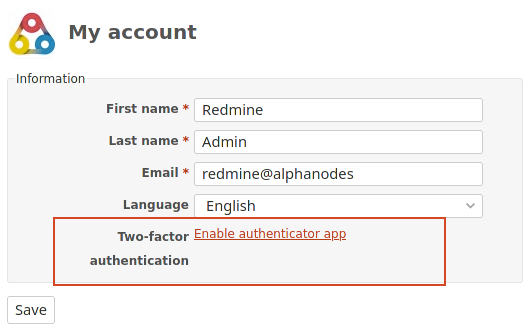
The current Redmine versions support two-factor authentication for user logins.
Manual detection and locking of inactive user accounts
Especially with a large number of users, it is difficult to keep track of active and inactive users. By default, users with administrator privileges can sort the Redmine user list by last login and decide whether to lock or delete someone.It becomes more convenient with the help of the Redmine HRM plugin. Here the user list is separated from the admin area. This allows users without admin rights but with special HRM permissions to manage (create, update, lock) users.
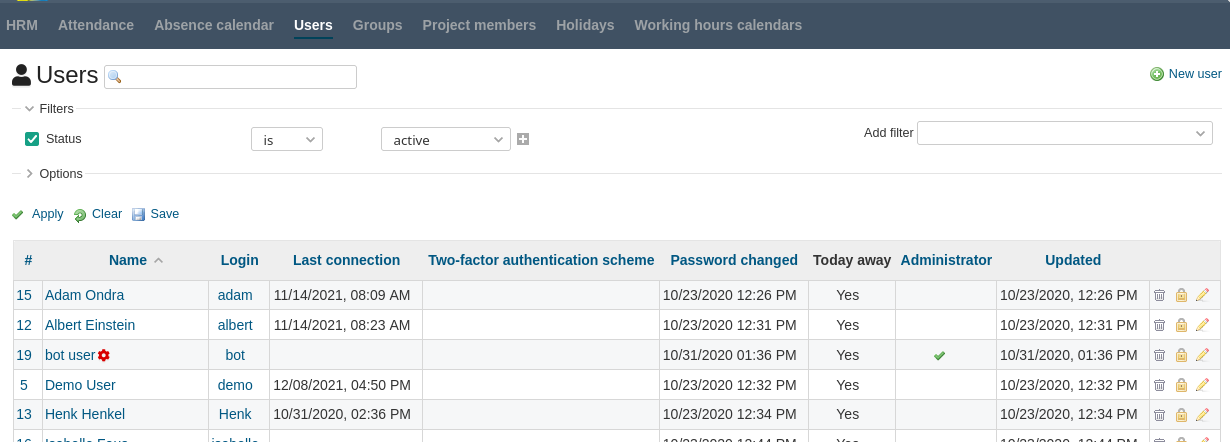
The user list of the HRM plugin provides many filters and options for conveniently managing users in Redmine.
This step is simplified with the help of additional filter options.
User accounts of employees should always be provided with a date field for leaving the company. This makes it easy to decide when a user account should be blocked. This is because the resignation date is offered as a filter.
User accounts of external users (customers, contractors, etc.) can also be provided with an end date. But, of course, track them by the date of their last activity or login. If an account has not been used for a longer period of time, one can temporarily block such accounts. The necessary filters for this are also available via the user list of the HRM plugin.
Tip: Save frequently used filters and options as user-defined query. Then this task will be faster for you.
Monitor conspicuous user activities
If you use the Redmine Reportin plugin, you have the possibility to monitor conspicuous user activities via an insight into the system-wide application log. You can also use the available filters to create your own custom query for regular monitoring. Activities to keep an eye on are for example:- frequently failed login attempts
- deletions of any kind (note: frequency, time period, by whom)
- updating user information
- Deletion of users
- Configuration updated
- Member created or deleted
- Adjustments made to roles (changed, created, deleted)
Automatically lock user accounts
If you use our Redmine Automation Plugin in addition to the HRM Plugin then you can automate certain actions like: Lock users, delete users, force password change at next login, as well as inform someone via email about a save event of a user account or login.
All information about our extensions for Redmine mentioned in this article is available on the product page. Customers whose Redmine does not meet the minimum requirements, or who prefer to hire someone to install and regularly maintain their Redmine instance, alternatively have the option to book our Managed Application Hosting for Redmine. Here the plugin offering from our company is already part of the hosting offer. The functionality can be tested extensively in our online demo. An overview of the features can be found here.
